Session Hijacking: A Rising Threat
What do you mean by session?
When you logged onto a website today, did it request for your username and password? If it did, did you notice it did not request for credentials while you utilized the website and browsed various pages? That's because once you've entered your credentials, you're essentially in a session that allows you to browse multiple pages without having to repeatedly enter your login details. To ensure a seamless and uninterrupted experience for users, web developers have implemented session cookies. These cookies securely maintain connections to authenticated websites, eliminating the need for constant reauthentication and providing a secure way to stay connected to the website you've logged into.
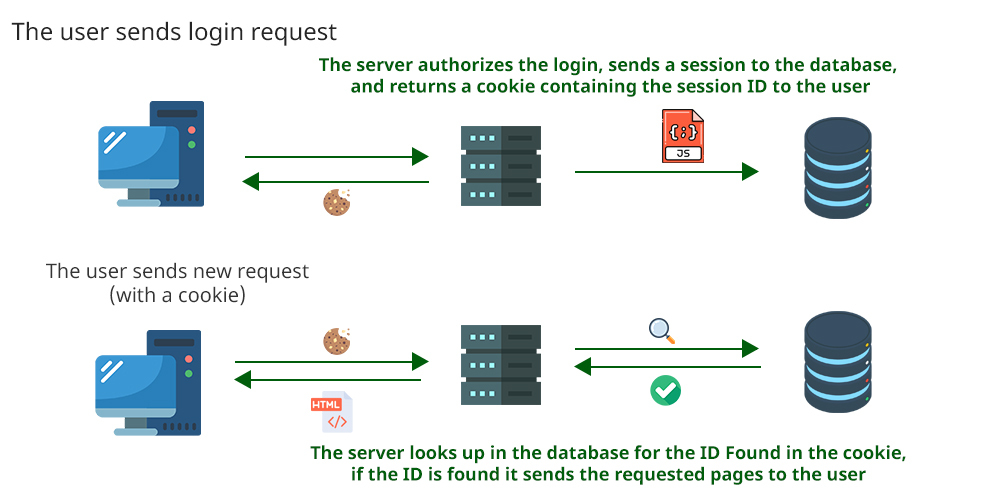
Lets take a look at the following image to show a visual explanation.
The top row demonstrates a new session being created.
On the left, the user's device signs into the web application or server. In the middle, the web application or server generates a session file with a unique ID in its database. Subsequently, the user receives a cookie from the web application or server, referencing this session with its unique ID.
The bottom row demonstrates an active session being authenticated against.
The user's device on the left accesses the web application or server using its active cookie, which contains the unique session ID. Within the system, the web application or server checks its database for an active session associated with this unique ID. Upon successful identification, the session is marked as valid, and a response is generated. Subsequently, the web application or server proceeds to load the requested web page for the user's device, ensuring seamless interaction and continuity in the browsing experience.
So then what is session hijacking?
Session hijacking occurs when a threat actor gains access to the cookie associated with your session on a specific website. Typically, this attack stems from the execution of malicious code on the user's device or from interactions with a malicious website. The attacker exports all cookies from detected browsers, sending them back to their own device. They then scrutinize the stolen cookies, targeting specific websites, and proceed to resume active sessions on their own devices. Below are examples of past incidents involving session hijacking.
Linus Tech Tips Youtube Channel and Google Account Hijacked via Malicious PDF
Office365 Customer Accounts Were Compromised and Utilized in Secondary Attacks
How can we prevent this?
The frontline of defense always rests with the user. From prevention measures to prompt alerting, it's crucial to train your users to recognize and respond to illegitimate access attempts or solicitations. Therefore, comprehensive phishing training is essential. For more insights on this subject, you can refer to our detailed post.
Relying solely on phishing training is insufficient, prompting organizations to reinforce their security posture through diverse measures. Below, we outline several solutions that can be implemented to proactively mitigate the risk of session hijacking attacks.
-
Email security solutions offer the capability to scan emails thoroughly, assessing the sender's legitimacy, detecting malicious attachments, and ensuring that any embedded links do not lead to malicious websites.
-
Antivirus solutions offer comprehensive scanning of recently downloaded files on user devices, preventing potentially harmful files from executing malicious code upon opening. Additionally, these solutions can isolate user devices from the corporate network if necessary. Furthermore, antivirus solutions provide advanced features akin to those of an Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) solution.
-
Implementing a web filtering solution empowers organizations to control access to websites based on reputation scores or predefined categories. These tools can effectively restrict access to sites that fail to meet established criteria, ensuring a safer browsing environment. Additionally, organizations can leverage these solutions to enforce specific restrictions, such as preventing file downloads or uploads on major websites.
-
Depending on the platform, you have the option to configure authentications to expire after a set duration. This proactive measure ensures that any compromised session IDs become invalidated, effectively thwarting unauthorized access attempts to the platform.
How do we detect if a session has been hijacked?
If a session hijacking incident occurs despite preventative measures, organizations typically have systems in place to reconstruct the attack's events and assess whether it has been effectively mitigated.
-
Most enterprise platforms offer organizations the ability to configure alerts for a wide range of events logged within the system. Enabling alerting for events such as new sign-on locations, changes to account information or credentials, modifications to platform settings, and the creation of reports allows organizations to identify potential compromises of user accounts by detecting trends in activity.
-
SIEM (Security Information and Event Management) solutions streamline the collection of system logs from various platforms into a centralized system. This consolidated data allows organizations to establish alerting mechanisms for any suspicious activities detected. Moreover, SIEM solutions can be configured to create user profiles and identify abnormal behavior, providing enhanced security measures against potential threats.
No perfect solution.
One of the most common insights gleaned from inquiries on this subject is the acknowledgment that "There is no perfect solution." The truth of cybersecurity is that perfection is unattainable, but there are excellent solutions available to organizations of all sizes. By leveraging these solutions, organizations can construct robust security stacks tailored to their specific needs and resources.
How can Hightower help?
Our recommendation to any client looking to understand potential deficiencies in their environment will always be our Technology Gap Assessment. Session hijacking is also a scenario we cover for our Tabletop Exercises that has been very popular over the last 2 years. If you are looking for general insight, we are happy to discuss options and strategy to position your organization to better understand and handle an attack like this.